Mastering The Realm: A Comprehensive Guide To Windows Server Kerberos Configuration
Mastering the Realm: A Comprehensive Guide to Windows Server Kerberos Configuration
Related Articles: Mastering the Realm: A Comprehensive Guide to Windows Server Kerberos Configuration
Introduction
With great pleasure, we will explore the intriguing topic related to Mastering the Realm: A Comprehensive Guide to Windows Server Kerberos Configuration. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Mastering the Realm: A Comprehensive Guide to Windows Server Kerberos Configuration
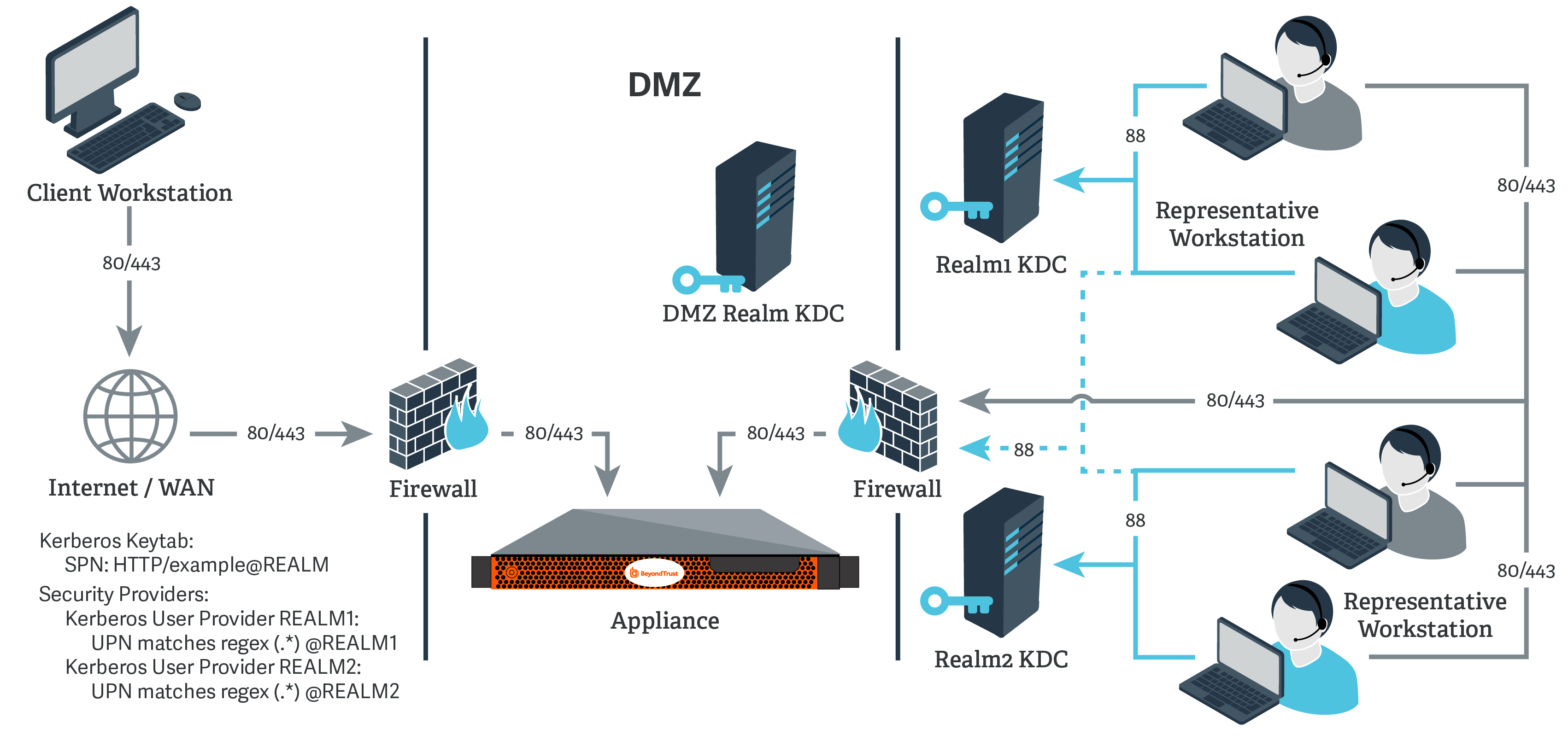
Kerberos, a powerful authentication protocol, forms the bedrock of secure communication within a Windows Active Directory environment. Its role in ensuring secure access to resources, services, and data is paramount, making a deep understanding of its configuration crucial for any system administrator. This article delves into the intricacies of Windows Server Kerberos configuration, providing a comprehensive guide to its implementation, troubleshooting, and optimization.
The Essence of Kerberos: A Secure Authentication Framework
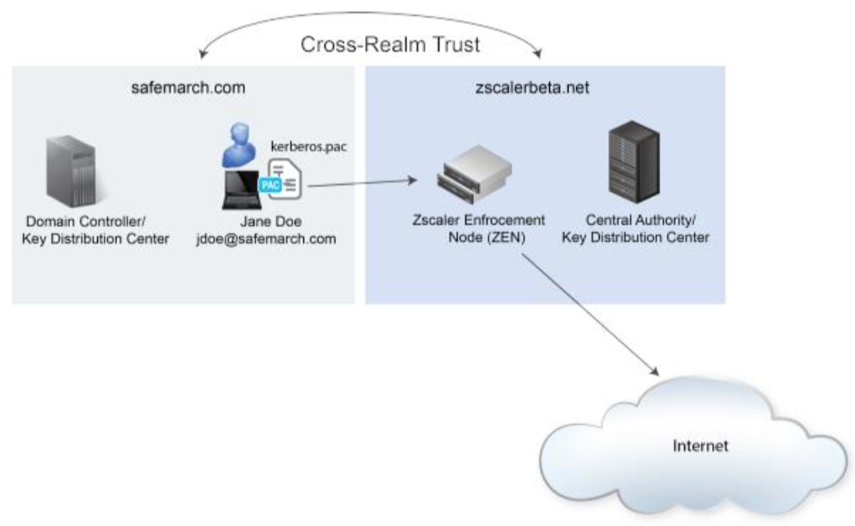
At its core, Kerberos operates on the principle of "mutual authentication," where both the client and server verify each other’s identities before granting access to resources. This process relies on a secure, centralized system known as the Key Distribution Center (KDC), which acts as the trusted authority within the domain.
Key Components of the Kerberos Ecosystem:
- Key Distribution Center (KDC): The central authority responsible for issuing and managing security keys (known as tickets) for users and services. It consists of two main components: the Authentication Server (AS) and the Ticket Granting Server (TGS).
- Authentication Server (AS): Handles the initial authentication request from a client, verifying the client’s credentials and issuing a Ticket Granting Ticket (TGT).
- Ticket Granting Server (TGS): Grants access to specific services based on the TGT provided by the AS. It issues Service Tickets, allowing clients to access specific resources.
- Clients: Users or applications requesting access to network resources.
- Servers: Services or applications that provide access to resources.
The Flow of Kerberos Authentication:
- Initial Authentication: A client requests access to a service.
- TGT Acquisition: The client sends a request to the AS, providing its username and password. The AS verifies the credentials and issues a TGT, encrypted with the client’s unique secret key.
- Service Ticket Request: The client presents the TGT to the TGS, requesting a Service Ticket for a specific service.
- Service Ticket Issuance: The TGS verifies the TGT, retrieves the service’s information, and generates a Service Ticket, encrypted with the service’s secret key.
- Service Access: The client presents the Service Ticket to the service, allowing access to the requested resource.
Configuration Essentials for a Robust Kerberos Environment:
1. Domain Controller (DC) Configuration:
- Domain Naming Context (DNS): Ensure proper DNS configuration for the domain, allowing clients to resolve the KDC’s hostname and IP address.
- Kerberos Domain Controller Settings: Configure settings such as the Kerberos realm, maximum ticket lifetime, and other domain-wide parameters.
- Time Synchronization: Accurate time synchronization across all DCs is critical for Kerberos to function correctly. Configure a time source like Network Time Protocol (NTP) for accurate timekeeping.
2. Client and Server Configuration:
- Kerberos Client Settings: Configure clients to trust the KDC and ensure proper communication with the domain.
- Kerberos Service Principal Names (SPNs): SPNs uniquely identify services within the domain. Configure SPNs for all services that require Kerberos authentication, ensuring proper mapping between the service and its corresponding account.
- Service Account Configuration: Create service accounts with appropriate permissions and configure them to use Kerberos authentication.
3. Security and Best Practices:
- Strong Passwords: Enforce strong password policies for user accounts and service accounts.
- Account Lockout Policies: Configure account lockout policies to prevent unauthorized access attempts.
- Kerberos Delegation: Utilize Kerberos delegation to allow services to act on behalf of users, simplifying authentication for complex scenarios.
- Kerberos Auditing: Implement Kerberos auditing to monitor authentication events and identify potential security vulnerabilities.
Troubleshooting Kerberos Issues:
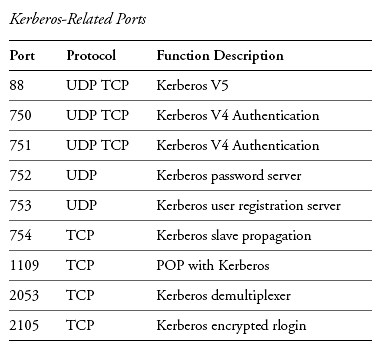
- Event Viewer: Use the Event Viewer to analyze Kerberos-related events, providing valuable insights into authentication failures.
- Kerberos Tools: Utilize built-in tools like Klist and Setspn to diagnose and manage Kerberos configuration.
- Network Connectivity: Ensure proper network connectivity between clients, servers, and the KDC.
- Time Synchronization: Verify accurate time synchronization across all components of the domain.
Frequently Asked Questions (FAQs):
Q: What is the purpose of Kerberos?
A: Kerberos is a network authentication protocol designed to provide secure access to network resources. It uses a system of tickets and secret keys to verify the identity of both clients and servers, ensuring secure communication and access control.
Q: Why is Kerberos important for Windows Server?
A: Kerberos is essential for Windows Server because it provides a secure and reliable authentication mechanism for accessing resources within a domain. It protects sensitive data, ensures user accountability, and simplifies access control management.
Q: What are the benefits of using Kerberos?
A: Kerberos offers several benefits, including:
- Strong Authentication: Provides secure authentication based on mutual verification of identities.
- Centralized Administration: Allows for centralized management of authentication policies and credentials.
- Scalability: Easily scales to accommodate large and complex networks.
- Interoperability: Works seamlessly with other Windows services and applications.
Q: How do I configure Kerberos on a Windows Server?
A: Configuring Kerberos involves configuring the domain controller, client machines, and services. This typically includes setting up DNS, creating service accounts, and configuring SPNs.
Q: What are some common Kerberos troubleshooting techniques?
A: Troubleshooting Kerberos issues often involves analyzing Event Viewer logs, using Kerberos tools like Klist and Setspn, and checking network connectivity and time synchronization.
Tips for Optimizing Kerberos Configuration:
- Use a dedicated domain controller for Kerberos operations.
- Configure Kerberos delegation for services that need to access resources on behalf of users.
- Implement Kerberos auditing to monitor authentication events and identify potential vulnerabilities.
- Regularly review and update Kerberos settings to ensure optimal security and performance.
Conclusion:
Kerberos stands as a cornerstone of security within a Windows Active Directory environment. Understanding its configuration, troubleshooting techniques, and best practices is essential for system administrators seeking to maintain a robust and secure network infrastructure. By mastering the realm of Kerberos, administrators can ensure secure access to resources, protect sensitive data, and enhance the overall security posture of their network.



Closure
Thus, we hope this article has provided valuable insights into Mastering the Realm: A Comprehensive Guide to Windows Server Kerberos Configuration. We hope you find this article informative and beneficial. See you in our next article!