Navigating Windows Server 2025 In A Post-TPM World: Understanding The Implications And Exploring Alternatives
Navigating Windows Server 2025 in a Post-TPM World: Understanding the Implications and Exploring Alternatives
Related Articles: Navigating Windows Server 2025 in a Post-TPM World: Understanding the Implications and Exploring Alternatives
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating Windows Server 2025 in a Post-TPM World: Understanding the Implications and Exploring Alternatives. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating Windows Server 2025 in a Post-TPM World: Understanding the Implications and Exploring Alternatives
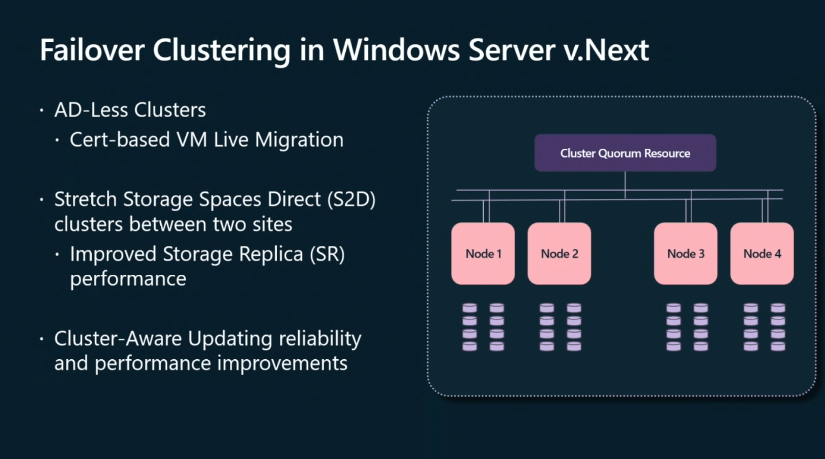
The landscape of cybersecurity is constantly evolving, and with it, the requirements for secure computing environments. One of the most prominent shifts in recent years has been the increasing emphasis on hardware-based security measures, exemplified by the growing prominence of Trusted Platform Modules (TPMs). While TPMs offer significant advantages in securing systems, their absence in legacy hardware or specific scenarios presents a unique challenge for organizations seeking to leverage the capabilities of Windows Server 2025.
This article delves into the implications of deploying Windows Server 2025 on systems without TPMs, exploring the underlying security considerations and potential workarounds. We will analyze the benefits of TPMs, discuss the limitations they impose on older hardware, and investigate alternative security strategies that can be implemented to maintain a robust and secure environment.
The Significance of TPMs in Modern Security
Trusted Platform Modules (TPMs) are specialized cryptographic chips embedded within computer systems. They play a crucial role in enhancing security by providing a secure environment for storing and managing cryptographic keys, facilitating secure boot processes, and enabling hardware-based encryption.
Key Benefits of TPMs:
- Secure Boot: TPMs ensure that only trusted operating systems and applications are loaded during the boot process, preventing malicious software from compromising the system before it can be detected.
- BitLocker Encryption: TPMs act as a hardware-based key protector for BitLocker Drive Encryption, making it significantly more difficult for unauthorized users to access encrypted data.
- Password Management: TPMs can securely store user passwords, preventing them from being compromised in the event of a system breach.
- Enhanced Authentication: TPMs enable stronger authentication mechanisms, such as Windows Hello for Business, which utilizes facial recognition or fingerprint scanning for secure login.
Challenges of TPM-less Environments
While TPMs offer significant security enhancements, their absence can present challenges for organizations:
- Legacy Hardware: Many older systems lack TPMs, making it difficult to implement the latest security features, including secure boot and BitLocker encryption.
- Cost Considerations: Upgrading existing hardware to include TPMs can be a costly endeavor, especially for large organizations with extensive server infrastructure.
- Limited Functionality: Without a TPM, certain security features, such as Windows Hello for Business and some advanced authentication protocols, may not be fully functional.
Navigating Windows Server 2025 Without TPMs: Exploring Alternatives
Despite the challenges, organizations can still deploy Windows Server 2025 on systems without TPMs while maintaining a high level of security. This requires a comprehensive approach that leverages a combination of software-based solutions, security best practices, and alternative security measures.
Software-Based Solutions:
-
Windows Server 2025 Security Features: Windows Server 2025 offers a robust set of built-in security features that can be effectively utilized even without a TPM. These include:
- Strong Passwords and Multi-Factor Authentication: Enforce strong password policies and implement multi-factor authentication (MFA) to strengthen user accounts.
- Group Policy and User Rights Management: Utilize Group Policy to configure security settings and restrict user privileges, limiting the potential impact of malicious activity.
- Security Updates and Patching: Keep systems updated with the latest security patches to address vulnerabilities and mitigate potential threats.
- Anti-Malware and Endpoint Protection: Implement robust anti-malware solutions and endpoint protection software to detect and prevent malware infections.
- Alternative Encryption Solutions: While BitLocker Drive Encryption heavily relies on TPMs, alternative encryption solutions, such as VeraCrypt or LUKS, can be employed to secure data on systems without TPMs.
Security Best Practices:
- Network Segmentation: Isolate sensitive systems and applications on separate networks to limit the potential impact of breaches.
- Firewall Configuration: Configure firewalls to block unauthorized network access and filter traffic based on specific security rules.
- Data Backup and Recovery: Implement regular data backup and recovery procedures to minimize data loss in the event of a security incident.
- Security Awareness Training: Educate users about common security threats and best practices for protecting sensitive information.
Alternative Security Measures:
- Virtualization and Containerization: Leverage virtualization and containerization technologies to isolate applications and systems, reducing the potential impact of security breaches.
- Hardware Security Modules (HSMs): HSMs provide a hardware-based security solution that can be used as an alternative to TPMs for secure key management and encryption.
- Secure Enclaves: Modern processors often include secure enclaves, which are isolated regions within the processor that can be used to protect sensitive data and computations.
FAQs
Q: Can I still use BitLocker Drive Encryption without a TPM?
A: While BitLocker Drive Encryption is designed to leverage TPMs for key protection, it can be used in a "TPM-less" mode. This mode utilizes a recovery password or a USB key to encrypt and decrypt the drive. However, it is important to note that this mode is less secure than using a TPM, as the recovery password or USB key can be compromised.
Q: What are the risks associated with using Windows Server 2025 without a TPM?
A: Using Windows Server 2025 without a TPM can increase the risk of security breaches, as it eliminates the hardware-based security measures provided by TPMs. This can make systems more vulnerable to malicious software, unauthorized access, and data theft.
Q: Are there any specific security features that will be unavailable without a TPM?
A: Some security features, such as Windows Hello for Business and certain advanced authentication protocols, rely heavily on TPMs and may not be fully functional without them.
Q: What are some best practices for securing a Windows Server 2025 system without a TPM?
A: Implementing strong password policies, enabling multi-factor authentication, utilizing Group Policy to restrict user privileges, and keeping the system updated with the latest security patches are essential practices for securing a Windows Server 2025 system without a TPM.
Tips
- Assess Your Security Needs: Carefully evaluate your specific security requirements and determine the level of security that is necessary for your environment.
- Consider Hardware Upgrades: If possible, consider upgrading older systems to include TPMs to benefit from the enhanced security features they provide.
- Implement a Layered Security Approach: Utilize a combination of software-based solutions, security best practices, and alternative security measures to create a robust and multi-layered security strategy.
- Stay Informed About Security Trends: Keep abreast of emerging security threats and vulnerabilities to proactively address potential risks.
Conclusion
The absence of TPMs in legacy hardware or specific deployment scenarios does not preclude organizations from leveraging the capabilities of Windows Server 2025. By implementing a comprehensive approach that combines software-based solutions, security best practices, and alternative security measures, organizations can maintain a high level of security and protect their systems from potential threats. While TPMs offer significant advantages, their absence does not necessitate a compromise in security. By embracing a proactive and informed approach, organizations can effectively secure their Windows Server 2025 environments even without TPMs, ensuring the integrity and confidentiality of their data.




Closure
Thus, we hope this article has provided valuable insights into Navigating Windows Server 2025 in a Post-TPM World: Understanding the Implications and Exploring Alternatives. We thank you for taking the time to read this article. See you in our next article!