Remote Access And Management In Windows Server: A Comprehensive Guide
Remote Access and Management in Windows Server: A Comprehensive Guide
Related Articles: Remote Access and Management in Windows Server: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Remote Access and Management in Windows Server: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Remote Access and Management in Windows Server: A Comprehensive Guide
- 2 Introduction
- 3 Remote Access and Management in Windows Server: A Comprehensive Guide
- 3.1 The Power of Remote Access: Enhancing Efficiency and Flexibility
- 3.2 Understanding Remote Access Technologies
- 3.3 Security Considerations for Remote Access
- 3.4 Best Practices for Remote Access
- 3.5 FAQs
- 3.6 Conclusion
- 4 Closure
Remote Access and Management in Windows Server: A Comprehensive Guide

This document provides a comprehensive overview of remote access and management capabilities within the Windows Server ecosystem, focusing on the technologies and practices that enable efficient and secure remote administration. While a specific release date for "Windows Server 2025" is not yet available, this exploration of remote access strategies remains relevant and applicable to future Windows Server releases.
The Power of Remote Access: Enhancing Efficiency and Flexibility
Remote access is a cornerstone of modern IT infrastructure, empowering administrators to manage and interact with servers and applications from anywhere with an internet connection. This capability is crucial for:
- Reduced Downtime: Remote access allows for swift troubleshooting and problem resolution, minimizing service disruptions and maximizing uptime.
- Increased Productivity: Administrators can manage multiple servers and environments remotely, eliminating the need for physical presence at each location.
- Simplified Deployment: Remote access facilitates the deployment of new servers, software updates, and configurations without requiring on-site personnel.
- Enhanced Security: Remote access can be implemented with robust security measures, limiting physical access to sensitive systems and enhancing overall security posture.
Understanding Remote Access Technologies
Windows Server offers a range of technologies for remote access and management, each with its own strengths and use cases:
1. Remote Desktop Protocol (RDP):
RDP is the primary protocol for establishing secure remote connections to Windows servers. It enables users to interact with the server’s graphical user interface (GUI) as if they were physically present at the console. RDP offers:
- High Fidelity: RDP provides a seamless remote experience, replicating the server’s desktop environment with fidelity, including graphics, audio, and peripheral support.
- Strong Security: RDP uses encryption and authentication mechanisms to protect data transmission and ensure only authorized users can connect.
- Wide Compatibility: RDP is supported by a wide range of operating systems and devices, making it a versatile solution for diverse environments.
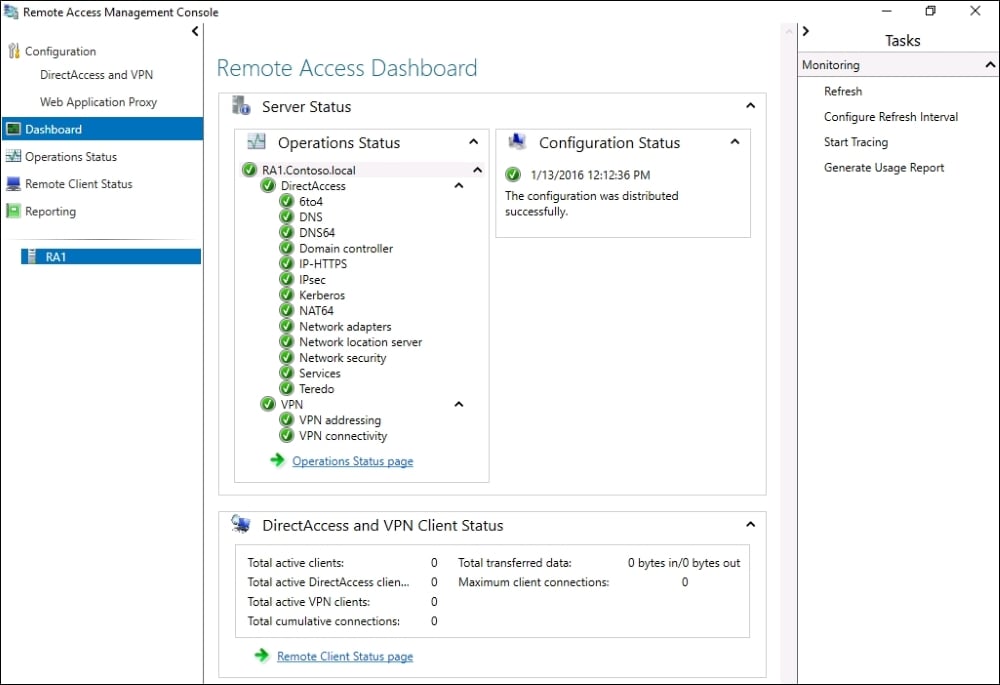
2. Windows Admin Center:
Windows Admin Center is a browser-based management tool that provides a centralized interface for managing Windows servers and other infrastructure components. It offers:
- Unified Management: Admin Center consolidates various management tasks, simplifying administration and reducing the need for multiple tools.
- Visual Interface: Admin Center presents a user-friendly interface with intuitive dashboards and visualizations, simplifying complex tasks.
- Remote Connectivity: Admin Center enables remote connections to servers, allowing administrators to manage them from anywhere.
3. PowerShell Remoting:
PowerShell Remoting allows administrators to execute PowerShell commands on remote computers, providing a powerful scripting interface for automation and management. It offers:
- Automated Tasks: PowerShell Remoting enables scripting complex tasks, automating administrative processes and minimizing manual intervention.
- Scalability: PowerShell Remoting can manage large numbers of servers with ease, facilitating efficient administration across distributed environments.
- Flexibility: PowerShell Remoting supports a wide range of operations, from basic configuration changes to complex deployments and updates.
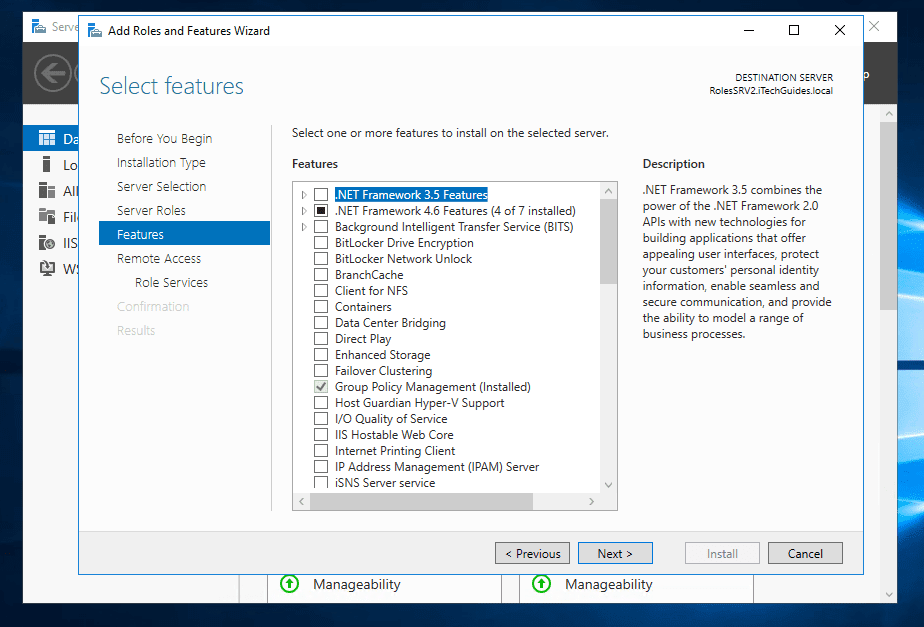
4. Server Manager:
Server Manager is a GUI-based tool for managing Windows servers locally or remotely. It provides a centralized interface for:
- Server Configuration: Server Manager allows administrators to configure server roles, features, and settings, simplifying initial setup and ongoing management.
- Monitoring and Reporting: Server Manager provides tools for monitoring server health, performance, and event logs, enabling proactive problem identification and resolution.
- Remote Access: Server Manager enables remote connections to servers, allowing administrators to manage them from other locations.
Security Considerations for Remote Access
While remote access offers numerous advantages, it also introduces security risks. Implementing strong security measures is essential to protect remote connections and sensitive data:
- Strong Authentication: Use multi-factor authentication (MFA) for all remote access, requiring users to provide multiple forms of verification, such as a password and a one-time code.
- Network Segmentation: Isolate remote access networks from the internal network, limiting potential attack vectors and protecting sensitive data.
- Access Control: Implement granular access controls to restrict user permissions based on roles and responsibilities, ensuring only authorized individuals can access specific resources.
- Regular Security Audits: Regularly review security policies and configurations, ensuring they remain effective and aligned with industry best practices.
- Firewall Rules: Configure firewall rules to block unauthorized access attempts and restrict traffic to authorized ports and protocols.
- Endpoint Security: Implement endpoint security solutions, such as antivirus software and intrusion detection systems, to protect remote devices from malware and malicious activity.
Best Practices for Remote Access
- Use a Secure VPN: Employ a Virtual Private Network (VPN) to encrypt all remote traffic, ensuring secure communication between the remote device and the server.
- Enable Network Level Authentication (NLA): NLA requires authentication before establishing an RDP connection, preventing unauthorized access and protecting against brute-force attacks.
- Keep Software Up-to-Date: Regularly update operating systems, applications, and security patches to mitigate vulnerabilities and protect against known exploits.
- Use Strong Passwords: Encourage users to create strong, unique passwords for all remote access accounts and avoid sharing credentials.
- Implement Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring users to provide a second form of authentication, such as a one-time code from a mobile device, in addition to a password.
- Use a Dedicated Account: Create a dedicated account for remote access, minimizing the risk of compromising other user accounts.
- Monitor Remote Access Activity: Track and review remote access logs regularly to identify suspicious activity and ensure compliance with security policies.
FAQs
Q: How can I access a Windows Server remotely?
A: To access a Windows Server remotely, you can use various methods, including:
- RDP: Use the Remote Desktop Connection (RDP) client to connect to the server’s graphical user interface.
- Windows Admin Center: Utilize Windows Admin Center’s web-based interface to manage the server remotely.
- PowerShell Remoting: Employ PowerShell Remoting to execute commands and scripts on the server from a remote machine.
- Server Manager: Use Server Manager to manage the server remotely through its graphical interface.
Q: What are the security considerations for remote access?
A: Security is paramount when implementing remote access. Key considerations include:
- Strong Authentication: Use MFA for all remote access, requiring users to provide multiple forms of verification.
- Network Segmentation: Isolate remote access networks from the internal network to limit potential attack vectors.
- Access Control: Implement granular access controls to restrict user permissions based on roles and responsibilities.
- Regular Security Audits: Regularly review security policies and configurations to ensure effectiveness.
- Firewall Rules: Configure firewall rules to block unauthorized access attempts.
- Endpoint Security: Implement endpoint security solutions to protect remote devices from malware.
Q: What are some best practices for secure remote access?
A: Adhering to these best practices can significantly enhance the security of remote access:
- Use a Secure VPN: Employ a VPN to encrypt all remote traffic.
- Enable Network Level Authentication (NLA): Require authentication before establishing an RDP connection.
- Keep Software Up-to-Date: Regularly update operating systems, applications, and security patches.
- Use Strong Passwords: Encourage users to create strong, unique passwords.
- Implement Two-Factor Authentication (2FA): Add an extra layer of security with 2FA.
- Use a Dedicated Account: Create a dedicated account for remote access.
- Monitor Remote Access Activity: Track and review remote access logs regularly.
Conclusion
Remote access is a powerful tool for managing Windows servers, offering significant benefits in terms of efficiency, productivity, and security. By understanding the available technologies, implementing strong security measures, and adhering to best practices, organizations can leverage remote access to streamline operations, enhance collaboration, and optimize their IT infrastructure. As Windows Server continues to evolve, the importance of remote access and management will only increase, necessitating a proactive approach to security and best practices.




Closure
Thus, we hope this article has provided valuable insights into Remote Access and Management in Windows Server: A Comprehensive Guide. We appreciate your attention to our article. See you in our next article!